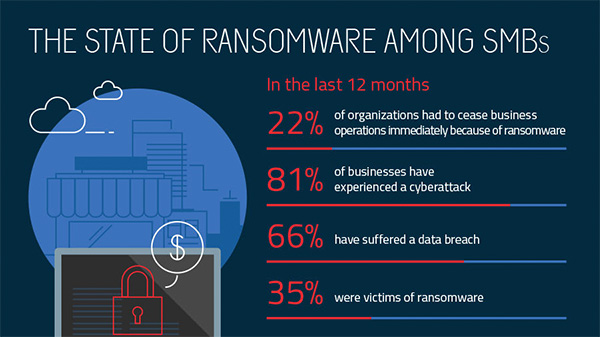
Ransomware is the latest in malware. Cyber criminals hijack your network and demand payment in order to unlock or decrypt your data.
The authors of these malicious threats have a very strong financial motive for infecting as many computers as possible, and have put substantial resources into making these threats prevalent. New variants are seen all the time. This infection is typically spread through emails sent to corporate email addresses, pretending to be from an array of legitimate companies. These emails would contain an attachment that, when opened, infects the computer. These .zip attachments contain executables that are disguised as PDF files: they have a PDF icon and are typically named something like FORM_101513.pdf.exe. Since Microsoft does not show extensions by default, they look like normal PDF files and trick victims into opening them. Once it is on the computer, Trojan.CryptoLocker will contact a "secret server" (Command and Control server) and generate a unique key with which to encrypt the victim's files. If it is able to generate a key, Trojan.CryptoLocker will then begin to sabotage all the MS Office documents. Open Office documents, and other valuable materials it can. Both files on the local computer and on any mapped network shares can be affected. Once the encryption is complete, the threat will display a pop-up which explains what it has done and demand payment for those files to be decrypted. It may also change the Windows desktop.